Introduction
The tragic crash of Air India Flight AI171, a Boeing 787 en route from Ahmedabad to London, has raised numerous questions, including some from the cybersecurity community:
Could this catastrophic event have been the result of a cyberattack?
In this post, we’ll explore that possibility from a technical architecture perspective. Specifically, we’ll examine:
- The distinction between mechanical and electronically actuated systems on the Boeing 787,
- The physical safeguards designed to prevent accidental or unauthorized manual actuation,
- And, crucially, why a cyberattack is highly improbable as the root cause of this particular sequence of events.
System Architecture: What Can Be Controlled Electronically vs. Manually?
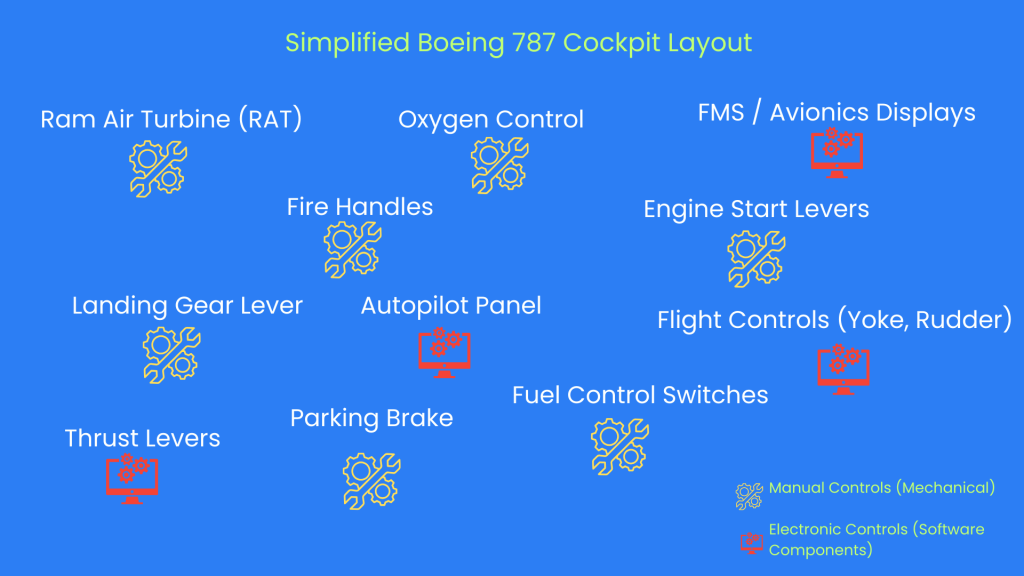
Modern aircraft like the Boeing 787 rely on extensive fly-by-wire and digital systems. However, not all cockpit controls are equally exposed to electronic actuation.
Note: FADEC stands for Full Authority Digital Engine Control, a fully electronic system that manages engine performance parameters such as fuel flow, thrust, and ignition automatically, replacing traditional mechanical linkages.
| Component | Type of Actuation | Cyber Vulnerability |
|---|---|---|
| Fuel Control Switches (Engine 1 & 2) | Manual (Mechanical) | Not vulnerable — physical toggle required |
| Engine Start Levers / Cutoff Switches | Manual (Mechanical) | Not vulnerable — isolated physical mechanism |
| Fire Handles / Fire Extinguisher Controls | Manual (Mechanical) | Not vulnerable — guarded physical actuation |
| Manual Landing Gear Lever | Manual (Mechanical) | Not vulnerable — mechanical lever with fail-safe |
| Parking Brake Handle | Manual (Mechanical) | Not vulnerable — isolated mechanical valve |
| Ram Air Turbine (RAT) Manual Deploy Handle | Manual (Mechanical) | Not vulnerable — manual cable actuation |
| Emergency Oxygen Deployment Control | Manual (Mechanical) | Not vulnerable — cable/switch mechanism |
| Throttle / Thrust Lever | Electronic (FADEC) | Potentially vulnerable — software-controlled |
| Primary Flight Controls (Yoke, Rudder, etc.) | Electronic (Fly-by-wire) | Potentially vulnerable — software-controlled |
| Flight Management System (FMS), Avionics Displays | Electronic | Potentially vulnerable — software-controlled |
| Autopilot | Electronic | Potentially vulnerable — software-controlled |
This architecture deliberately isolates critical manual controls like fuel cutoff switches from digital systems.
Physical Security Controls for Manual Actuation
The fuel control switches that shut off fuel to the engines are a prime example of a deliberately manual control:

- Guardrails / Protective Covers:
- These switches are surrounded by an aluminum mechanical guard structure.
- This ensures that a pilot cannot accidentally knock them into the CUTOFF position while operating other controls.
2. Spring-Loaded Latch Mechanism:
- There’s a spring mechanism built in that requires a deliberate lift before the switch can move.
- This provides a tactile, physical safeguard to prevent accidental toggling due to poor ergonomics or distraction.
These critical controls have no electronic actuation path and include physical safeguards (guards, spring-loaded latches, tactile (giving sense of touch) design) that require deliberate human action.
This architectural principle is supposed to maintain human authority even in extreme scenarios such as total electronic failure or attempted cyber compromise.
These design features reflect an important principle of aviation safety:
Critical engine shutoff mechanisms should require deliberate, unmistakable human action.
Could a Cyber Attack Cause This Sequence?
In this incident:
- The fuel control switches physically moved from RUN to CUTOFF just after takeoff, shutting down both engines within seconds.
- The cockpit voice recorder captured confusion between pilots, suggesting neither pilot knowingly commanded this sequence.
But based on the architecture above:
The fuel control switches are completely isolated from electronic systems and have no electronic actuation path and include physical safeguards (guards, spring-loaded latches, tactile (giving sense of touch) design) that require deliberate human action.
There is no software path for malware or unauthorized code to move these switches remotely.
Even malicious manipulation of fly-by-wire systems or avionics would not allow actuation of these switches.
This architectural principle is supposed to maintain human authority even in extreme scenarios such as total electronic failure or attempted cyber compromise.
Therefore:
The hypothesis of a cyberattack directly causing the fuel control switches to move is technically implausible.
What Components Could a Cyberattack Impact on the Boeing 787?
While a cyberattack is highly improbable for this specific failure mode, certain aircraft systems are, in principle, more exposed:
The table below summarizes key Boeing 787 components that could, in principle, be exposed to cyberattack, along with why they’re vulnerable and their likely attack vectors.
Component | Type of Vulnerability | Why Vulnerable? | Likely Attack Vector |
|---|---|---|---|
| Flight Management System (FMS) | Software compromise | Processes flight plan/navigation data electronically | Ground-based malware during maintenance upload or malicious data injection via ACARS/SATCOM |
| Autopilot / Flight Directors | Software compromise | Electronically commanded by flight control computers | Indirect compromise if FMS or flight control systems infected |
| Thrust Levers (via FADEC) | Software compromise | FADEC interprets thrust lever positions electronically | Possible compromise of FADEC firmware or upstream FMS inputs |
| Primary Flight Controls (fly-by-wire) | Software compromise | Controlled electronically by flight control computers | Indirect compromise if flight control computers compromised |
| Avionics Displays | Data integrity / spoofing | Depend on sensor/fleet data inputs | Malicious input injection or tampering of connected sensors/data feeds |
Important note: While these components are potentially exposed to cyber risks in principle, the Boeing 787 is not directly connected to the public internet. Possible attack vectors would generally involve indirect paths, such as malware introduced during maintenance via diagnostic tools or malicious data injection through connected systems like ACARS or SATCOM. Proper isolation and authentication mechanisms reduce practical exposure.
However:
- The fuel control switches remain a physically actuated, guarded, spring-loaded mechanism.
- They are explicitly designed to resist exactly this kind of unauthorized or inadvertent change — whether accidental or malicious.
Conclusion
The preliminary report on AI171 points to an asymmetric sequence of switch movements that is puzzling from both human factors and procedural perspectives.
But from a cybersecurity standpoint:
- The physical and architectural design of the Boeing 787 fuel control switches makes a cyberattack an improbable root cause for this event.
- If there were malicious intent, it would have had to involve either:
- Physical tampering with the switches prior to flight, or
- A very different attack surface (e.g., misleading data to pilots, not actuating physical switches).
Disclaimer: This article provides a technical cybersecurity analysis of Boeing 787 cockpit architecture and control systems. It does not speculate on the cause of the AI171 accident, assign blame, or draw conclusions beyond the cybersecurity perspective. The discussion is intended solely to explain which systems are potentially exposed to cyber risk and which are isolated by design.



Leave a reply to Kamlakar Kadam Cancel reply