Introduction
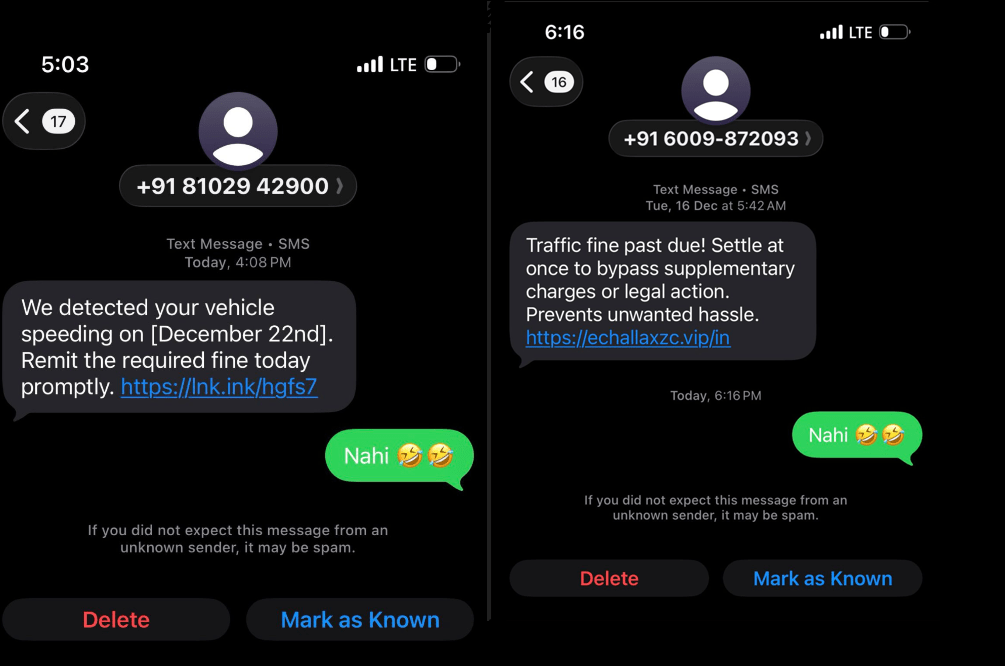
A recent SMS phishing campaign disguised as an “e-challan” notification demonstrates how attackers exploit urgency and government branding to trick victims. When a user visits the link, nothing appears to happen on the surface; the page simply sits on Cloudflare’s “verifying human” screen. However, silently in the background, a file is dropped onto the user’s system which begins querying saved passwords and form data, targeting Windows systems specifically to steal credentials and browser data.
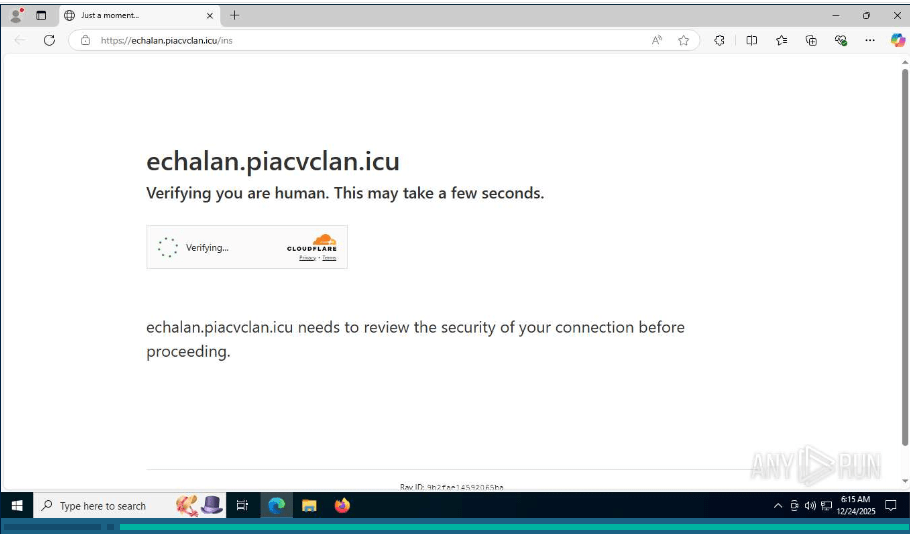
Delivery Vector
Victims received an SMS claiming overspeeding violations, urging them to click a link to view their challan. The link redirected to a suspicious domain protected by Cloudflare verification, masking its malicious intent.
Sanbox Analysis
- Android Sandbox (ANY.RUN): The link resolved to a Cloudflare verification page, with no APK delivered during the test. This suggests conditional payload delivery or phishing-only behavior for mobile devices.
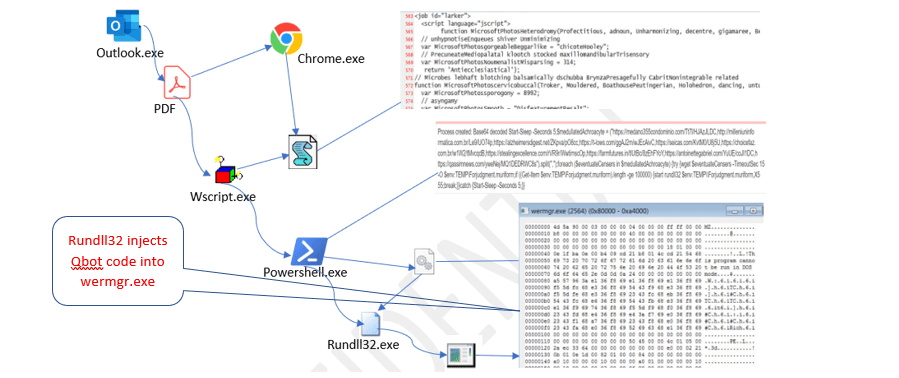
- Windows Sandbox (ANY.RUN): Executing the payload in a Windows VM revealed low-level NT API calls (
NtCreateFile,NtReadFile,NtQueryInformationFile) targeting Chrome’sUser Data\Defaultdirectory. Files accessed includedLogin Data,Cookies, andFavicons.
Malware Behaviour
- Credential Theft: The malware attempted to read Chrome’s SQLite databases containing saved passwords and session cookies.
- Stealth Techniques: By using native NT APIs, the malware bypassed common AV hooks and sandbox detection.
- Cobalt Strike Beaconing: A downloaded file (hash:
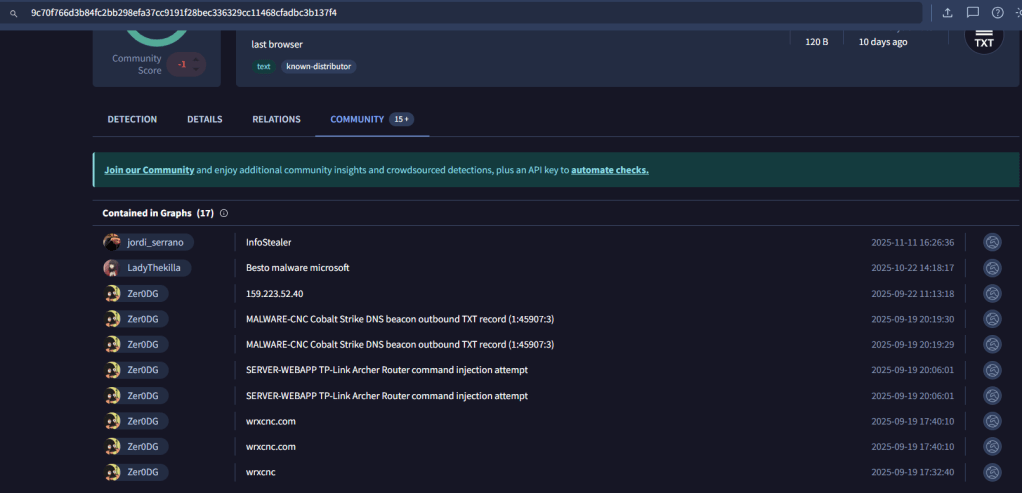
9c70f766d3b84fc2bb298efa37cc9191f28bec336329cc11468cfadbc3b137f4) was flagged on VirusTotal as an InfoStealer and linked to Cobalt Strike DNS beaconing, indicating potential remote access and post-exploitation capabilities.
Platform Impact
- Windows: Primary target, with payload designed to steal browser credentials and establish C2 communication.
- Android/iOS: SMS lure works cross-platform, but payload delivery is conditional. Mobile users may encounter phishing pages or APKs depending on device fingerprinting.
Indicators of Compromise (IOCs)
- Domains:
echalan.piacvclan.icu - File Hash:
9c70f766d3b84fc2bb298efa37cc9191f28bec336329cc11468cfadbc3b137f4 - Behavior: Access to Chrome
User Data\Defaultfolder, DPAPI decryption attempts, DNS beaconing.
Defensive Recommendations
- Block and monitor suspicious domains and short-link services.
- Educate users on SMS phishing tactics exploiting urgency and government branding.
- Enforce browser hygiene: clear cookies, rotate passwords, enable MFA.
- Monitor for Cobalt Strike beaconing and unusual DNS TXT queries.
Conclusion
This campaign highlights how attackers leverage SMS as a universal lure while tailoring payloads to specific platforms. The Windows variant demonstrates a clear focus on credential theft and remote access, underscoring the need for vigilant monitoring and user awareness.
Screenshots and Reports Placeholders
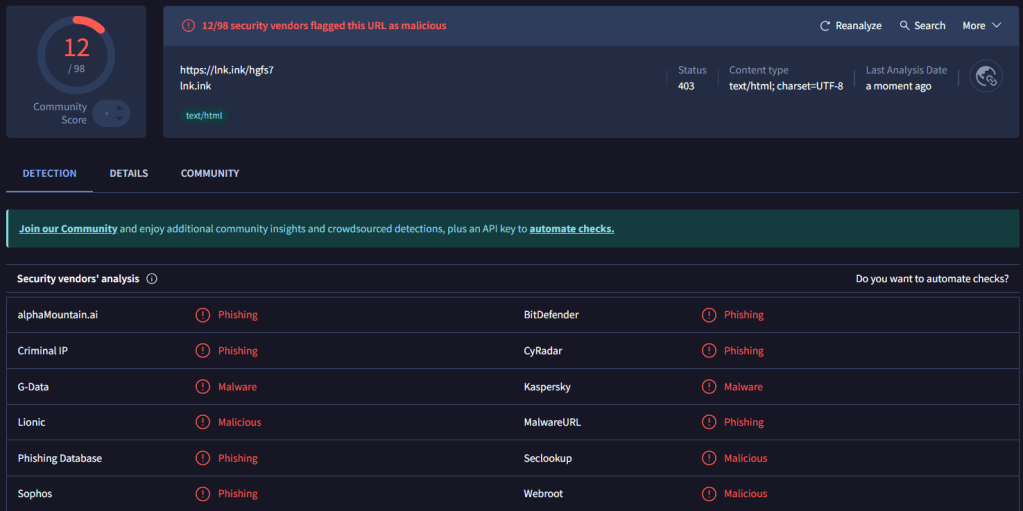
VirusTotal URL analysis
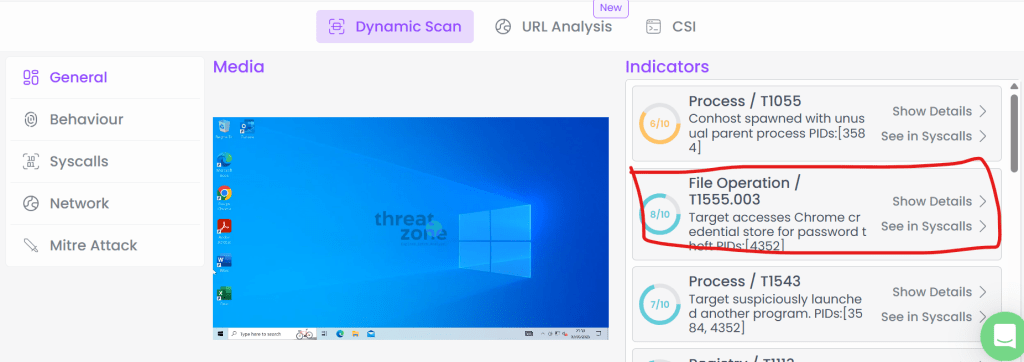
ThreatZone Analysis confirms payload tragetting saved passwords in browsers
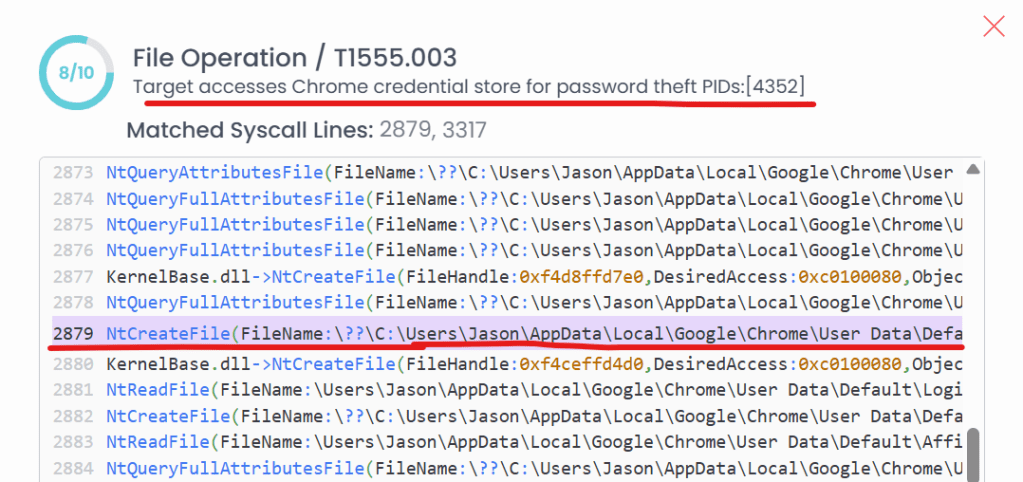
Any Run Sandbox Confirmes file drop
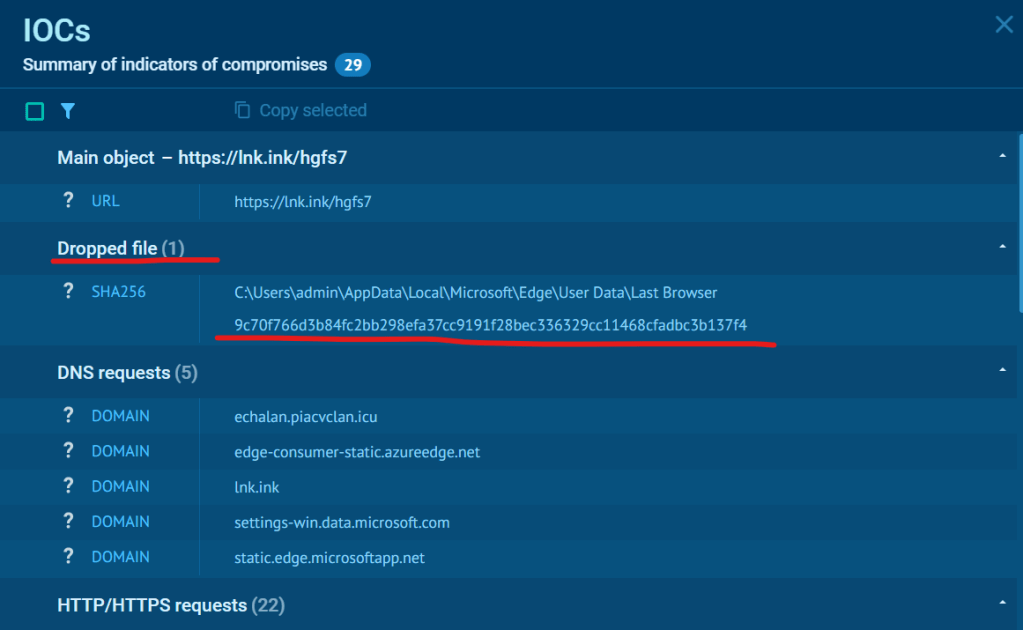
Virustotal Community Response to dropped file


Leave a comment