In May 2021, the Colonial Pipeline ransomware attack disrupted fuel supply across the Eastern United States, triggering emergency declarations and public panic. While the attack was executed by the DarkSide ransomware group, its implications for industrial cybersecurity were profound—especially for OT environments.
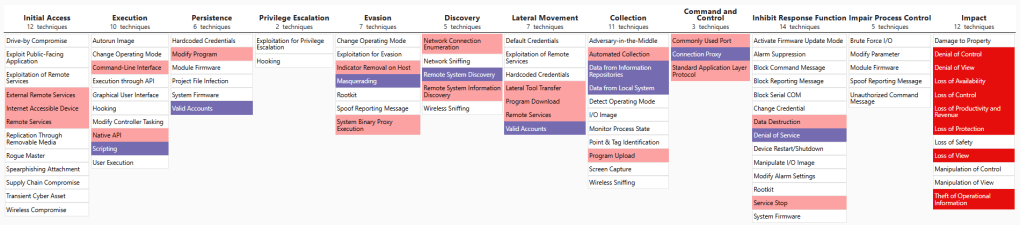
To help learners and practitioners understand the anatomy of such an attack, I mapped the tactics and techniques used in the Colonial incident to the MITRE ATT&CK for ICS framework. This mapping provides a structured lens to analyze how adversaries penetrate, persist, and impact industrial systems.
MITRE ICS Tactics and Techniques Observed
Here’s a snapshot of how the attack aligns with MITRE ICS tactics:
| Tactic | Techniques Used |
|---|---|
| Initial Access | External Remote Services, Internet Accessible Device, Remote Services |
| Execution | Command-Line Interface, Scripting, Native API |
| Persistence | Modify Program, Valid Accounts |
| Evasion | Masquerading, Indicator Removal on Host, System Binary Proxy Execution |
| Discovery | Network Connection Enumeration, Remote System Discovery, Remote System Info Discovery |
| Lateral Movement | Lateral Tool Transfer, Program Download, Remote Services, Valid Accounts |
| Collection | Automated Collection, Data from Information Repositroies, Data from Local System, Program Upload |
| Command and Control | Commonly Used Port, Connection Proxy, Standard Application Layer Protocol |
| Inhibit Response Function | Data Destruction, Denial of Service, Service Stop |
| Impact | Denial of Control, Denial of View, Loss of Availability, Loss of Control, Loss of Productivity and Revenue, Loss of Protection, Theft of Operational Information |
Sources include CISA, FBI, TrendMicro, and Cybereason analyses of the DarkSide ransomware campaign.
Why This Mapping Matters
- Operational Relevance: MITRE ICS helps defenders think in terms of real-world OT workflows, not just IT-centric indicators.
- Defense Prioritization: By identifying which tactics were used, organizations can prioritize detection and mitigation strategies.
- Training Value: This mapping is a powerful teaching tool—especially for engineers transitioning into cybersecurity roles.
If you found this post insightful and want to explore more real-world OT security scenarios, check out my full course on Udemy: “Practical OT Cybersecurity for Engineers and Architects”. It’s packed with demos, analogies, and actionable strategies to help you secure industrial environments.


Leave a comment