Introduction
In July 2025, Citrix NetScaler was struck by a high-severity vulnerability — CVE‑2025‑5777, now dubbed Citrix Bleed 2. This flaw allowed attackers to access sensitive memory contents, including session tokens, credentials, and other internal data — even without authentication.
So what made this bug so devastating, and yet so simple to exploit?
The root cause lies in a small yet dangerous oversight in C programming: an uninitialized variable.
How can one line of C code—left carelessly incomplete—leak critical data like session tokens? That’s what we explore in this post, using Citrix Bleed 2 as our case study
What You’ll Learn:
- How CVE‑2025‑5777 (Citrix Bleed 2) works
- Why uninitialized variables in C/C++ are risky
- Differences in memory handling between C/C++ and higher-level languages like Python
- Secure coding practices to prevent such vulnerabilities
- Conceptual fix for the vulnerability using safe defaults
Citrix Bleed 2 CVE-2025-5777 as a reference point for Secure Coding:
- Vulnerability: Sensitive memory exposure in NetScaler’s authentication process (authentication handler endpoint)
- Risk: Leak of sensitive data (e.g., credentials, session tokens) to unauthenticated attackers
- Threat action: Malformed POST request to /p/u/doAuthentication.do endpoint
- Cause: Uninitialized stack memory included in XML server response
- CVSS score: 9.3 ; Exploited before public PoC release
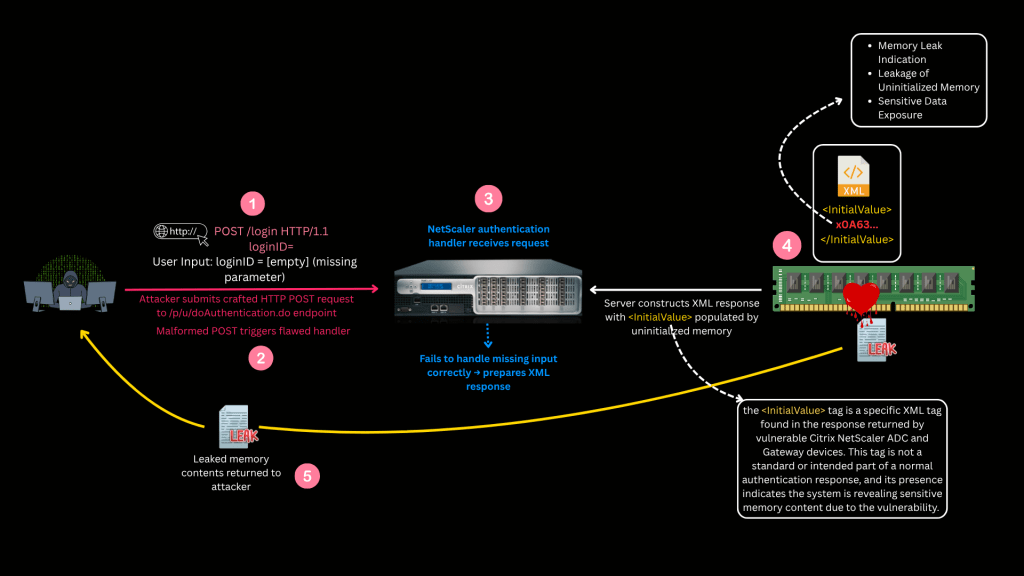
The flaw existed in Citrix’s authentication handler endpoint:
POST /p/u/doAuthentication.do
When an attacker sent a malformed HTTP POST request with a missing loginID parameter, the server failed to handle the input gracefully. Instead of rejecting the request, the server returned an XML response where the tag leaked uninitialized stack memory.
This is what made the attack possible — and it boiled down to a forgotten variable initialization.
To understand this vulnerability better, we need to go back to the basics — how memory works in low-level languages like C, what variables actually are, and what happens when a variable is left uninitialized. These seemingly small details can create a ripple effect that leads to serious real-world issues like Citrix Bleed 2.
Root Cause Breakdown: Citrix Bleed 2 & Uninitialized Memory
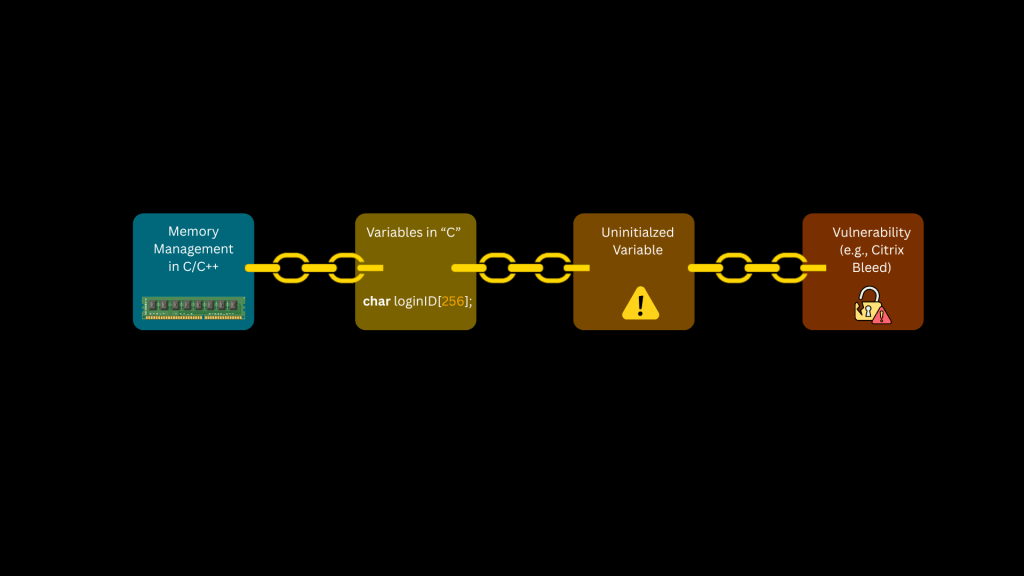
Memory Management in C (low-level) vs Python, Java (high-level) language
| C/C++ | Python, Java |
| C/C++: Developers must manage memory manually — from allocation to initialization and cleanup. | High-level lang such as Java, Python: manage memory automatically (garbage collection). |
| Forgetting to initialize can leave memory in an unpredictable state, leading to bugs and security issues. | Languages like Java, Python simplify development by abstracting memory management, making them ideal for many business applications and automation tasks |
| Low-level access to memory increases the chances of unintentional exposure (e.g., reading leftover data). | But when performance, memory control, or hardware-level access is critical — such as in OS kernels, device drivers, and embedded systems — C and C++ remain essential because they allow fine-grained, deterministic control and offer unmatched execution speed. |
Variables in C
In programming, a variable is a named storage location in memory that holds a value or data.

A variable can exist in two primary states: uninitialized and initialized.
- An uninitialized variable has been declared but has not yet been assigned a specific value.
- An initialized variable has been declared and assigned a specific value.

What’s the Risk of an Uninitialized Variable?
A variable in C (like char loginID[256]😉 allocates memory, but does not initialize it. So unless you assign it a value (char loginID[256] = “0”;), that memory can contain anything — including leftover data from previous operations.
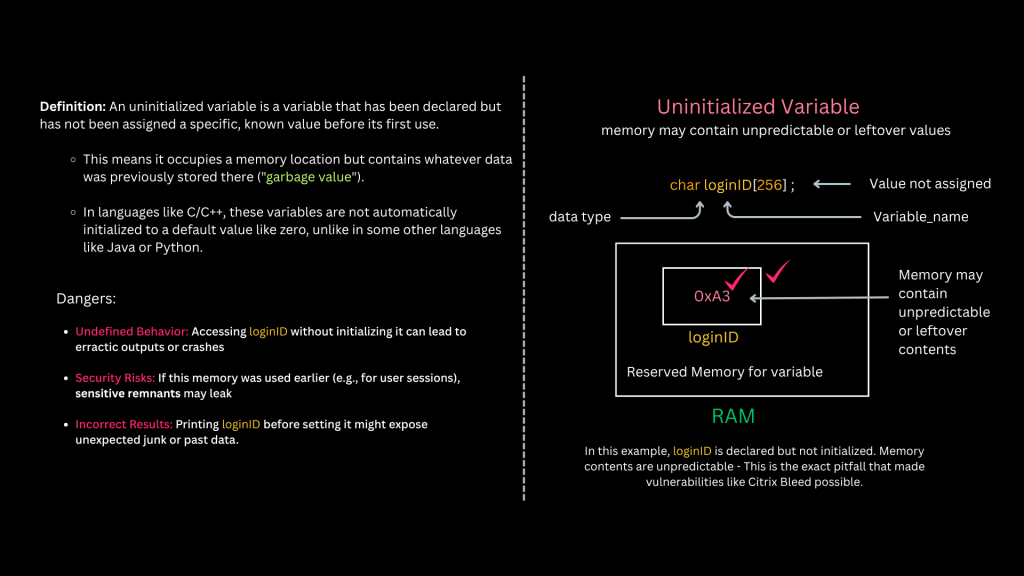
Uninitialized memory can expose:
- Session tokens
- Credentials
- Internal configuration info
And worse, these leaks can happen without crashing the program, making them stealthy and hard to detect.
Understanding the risk with two Scenarios:Safe vs Risky
1. Safe Case: User sends valid input → memory overwritten → response is clean
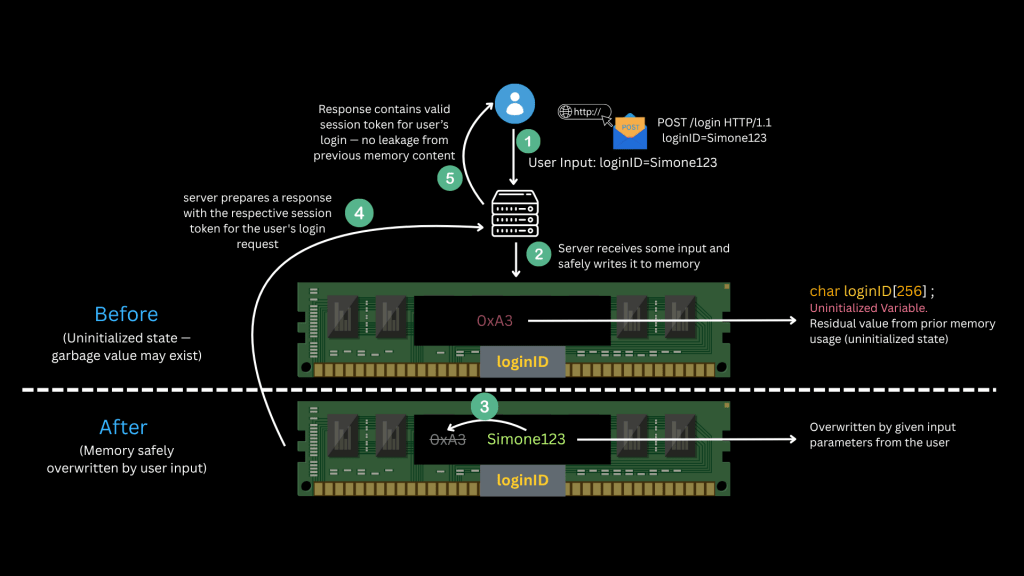
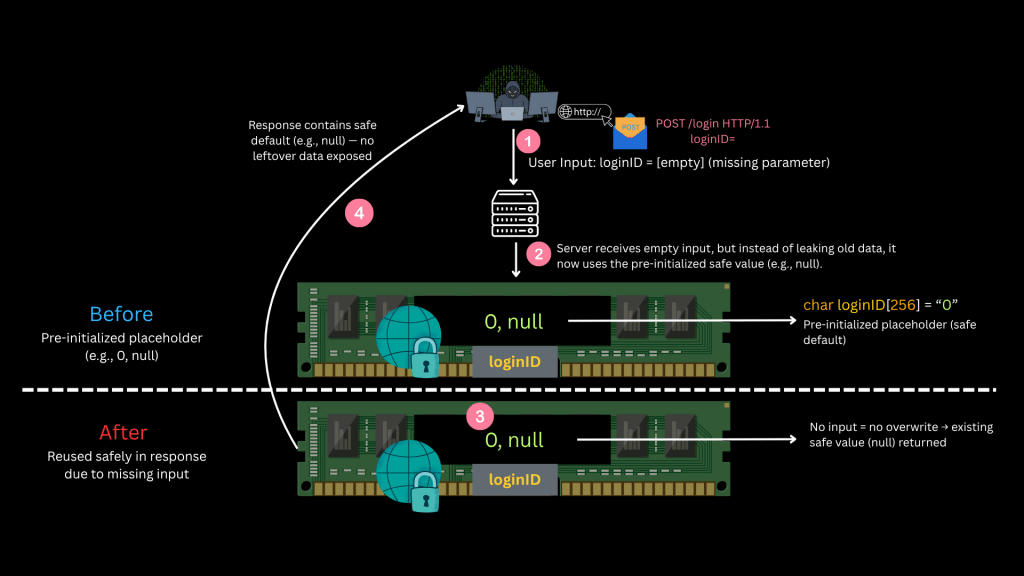
2. Risky Case: Attacker sends blank input → memory not overwritten → response leaks data

Mitigation Strategy: Proactive Initialization
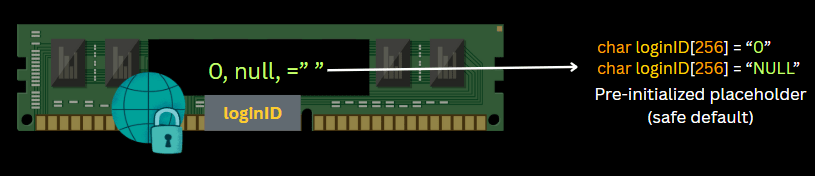
Always initialize variables with safe defaults like:
char loginID[256] = “NULL”;
This ensures that even if input is missing, the response won’t leak garbage data.
Why It Works:
- Valid input overwrites the default value safely.
- If input is missing, no stale data leaks — the program safely responds with a predefined value, avoiding memory leakage.
- Prevents uninitialized memory leaks (like in the Citrix Bleed vulnerability).
Here’s a replay of Scenario 2 after applying the mitigation, notice how the server now responds gracefully without leaking any memory, thanks to proper variable initialization
If you found this useful, check out the short and long video breakdowns where I demonstrate this with code and visuals. Links below!


Leave a comment