Welcome to Part 5 of the Advanced Malware Tactics series.
In this final part, we explore the groundbreaking research presented at Black Hat Europe 2023 that uncovered eight fully undetectable process injection techniques. These are not your average memory injection methods. Instead, they rely on a completely different execution strategy — leveraging Windows thread pools.
If you’ve been following Parts 1 to 4, you’ve built a solid foundation. Now let’s level up.
A Quick Recap of the Series So Far
Before diving into thread pool injection, let’s quickly recap what we’ve covered:
Part 1: We explored Windows OS internals and core concepts like user mode, kernel mode, processes, threads, and virtual memory — all

Part 2: We introduced process injection and discussed why attackers use it post-exploitation.

Part 3: We deep-dived into the building blocks of injection — allocation, writing, and execution.
Part 4: We examined DLL injection using a real-world example from the Qakbot malware campaign.
Now in Part 5, we study one of the new techniques that bypasses all modern EDRs using thread pool manipulation.
The Goal Behind This Research
Researchers set out to challenge the current EDR detection model. Most EDRs monitor execution primitives — they detect malicious behavior when payloads are executed (like with CreateRemoteThread).
But what if attackers skip the execution step entirely?
These researchers reverse-engineered Windows thread pools and figured out how to:
- Allocate memory
- Write malicious code
- Let legitimate system threads execute it naturally
That’s exactly what these thread pool injection techniques do.
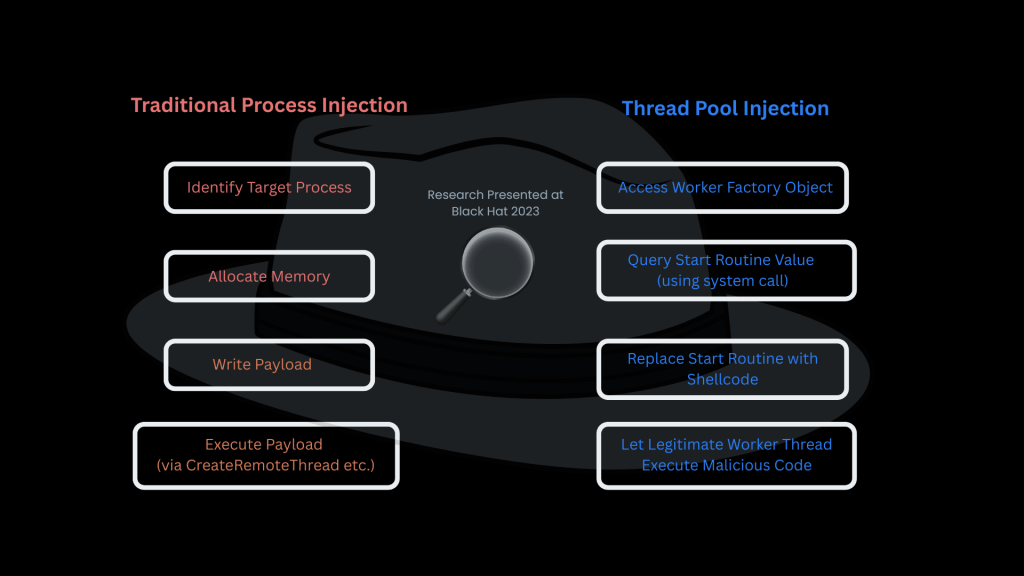
In traditional injection, attackers allocate memory, write a payload, and call an API to execute it (e.g., CreateRemoteThread). That last step triggers EDR alarms.
But thread pool injection, particularly the start routine value manipulation technique discovered and presented at Black Hat Europe, takes a fundamentally stealthier approach.
Instead of manually creating a new thread for executing the malicious payload, this technique hijacks an existing, legitimate worker thread within the target process’s thread pool. It manipulates the start routine value — essentially the agenda that tells the worker what task to perform — and replaces it with attacker-supplied shellcode.
As a result, the malicious code gets executed naturally by the target’s own thread, not as a foreign object or suspiciously spawned thread. This removes the need for invoking any suspicious APIs and makes detection by traditional EDR rules far more difficult.
This architectural exploitation leverages how thread pools are designed to improve performance and concurrency — ironically turning a legitimate feature into an effective evasion vector.
The key takeaway: No new thread is created. Instead, an existing trusted thread unknowingly executes malicious logic, blending in perfectly with normal process behavior.
Why Target the Thread Pool?
Before we jump into the internal components of the Windows thread pool, let’s pause and ask:
Why was the thread pool selected as a target for a novel process injection technique?

During their exploration for an ideal injection target, researchers were on the lookout for a system component that was:
- Widely present
- Consistently structured
- Capable of executing arbitrary code through internal, trusted mechanisms
And that’s when they found it — the Windows User-Mode Thread Pool.
Here’s why this made such a compelling target:
- Present in Every Process
All Windows processes are assigned a thread pool by default. This means that any technique capable of manipulating the thread pool architecture becomes instantly scalable across all Windows processes — an attacker’s dream.

- Structured Internals
Thread pools and their work items are implemented using structured memory layouts. This increases the likelihood that attackers can manipulate specific primitives (like the start routine pointer) without triggering detection based on behavior.

- Multiple Execution Paths
Modern thread pools are designed for high concurrency and multitasking. They support different types of work items, giving attackers more opportunities to hijack the thread pool’s behavior and redirect it toward executing malicious code.

- Complex and Dual-Mode Execution
The thread pool spans both user-mode and kernel-mode components. This complexity not only increases the attack surface but also makes detection more challenging for security tools that don’t monitor this dual-mode behavior deeply.
Revisiting Thread Pool Architecture (Simplified)
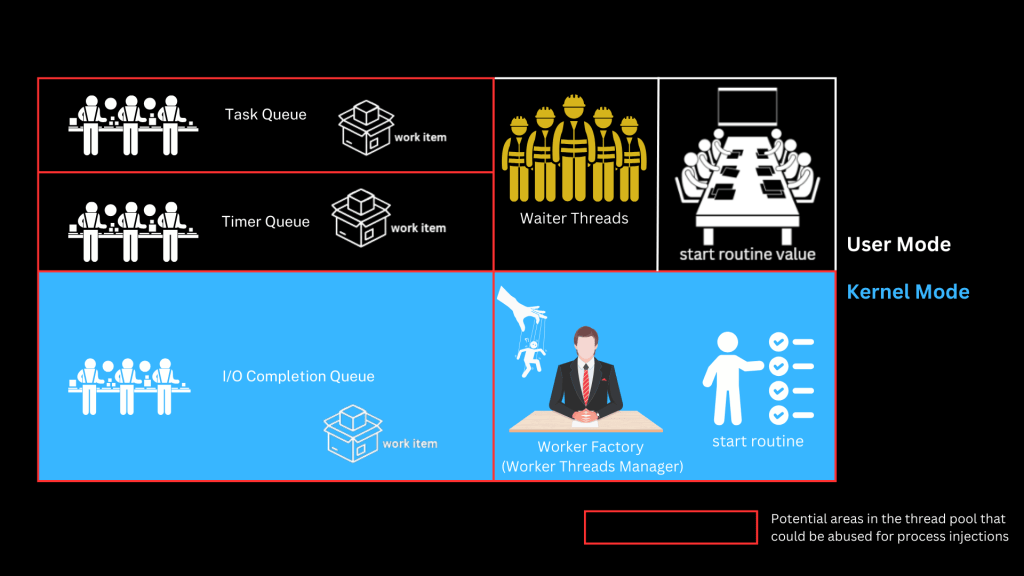
Windows uses thread pools to manage background worker threads for every process. Here’s a simplified breakdown:
Thread pools include:
- Worker threads: Perform tasks assigned via queues. Actual threads doing the work.
- Waiter threads: Wait for a signal/event and act afterward.
- Task queues, timer queues, I/O completion queues: Where tasks are lined up.
- Worker Factory object: Maintains an adequate number of worker threads. Like a manager, creates/destroys threads as needed.
- Start Routine: Instructions that each thread should follow
- Start Routine Value: Memory address pointing to the start routine i.e., where it’s located in memory.

The vulnerability lies in how predictable and accessible the Start Routine Value is — this tells you exactly where in memory a thread’s instructions live.
Attackers target these components, especially the Start Routine Value — by replacing it with shellcode, they hijack the behavior of worker threads without raising red flags.
Total of 8 Novel Techniques – But We Focus on One
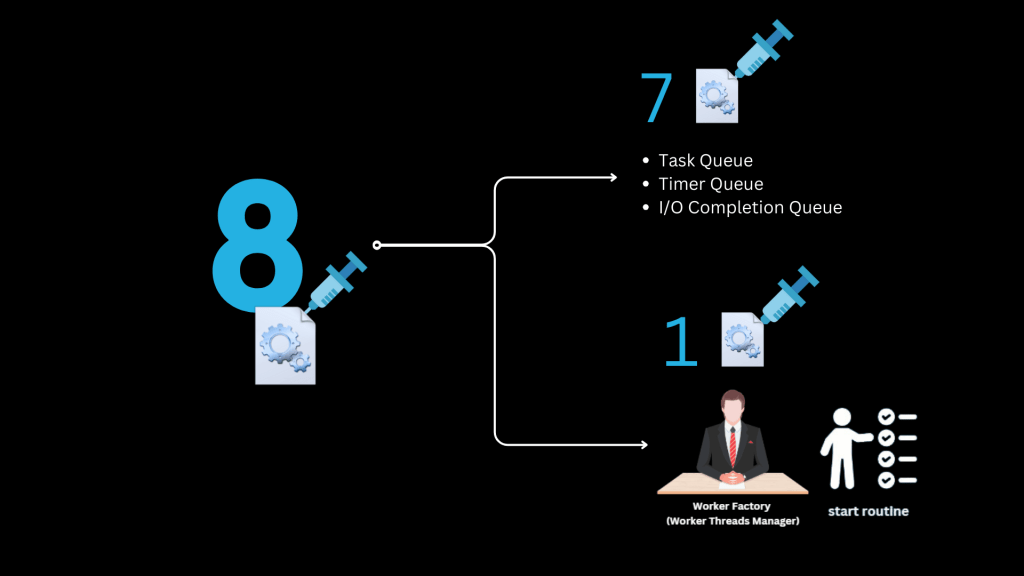
The research presented at Black Hat Europe unveiled 8 brand-new process injection techniques – all leveraging the Windows thread pool architecture.
Out of these eight:
- 1 technique focuses on the Worker Factory – specifically manipulating its knowledge of the start routine location.
- The other 7 techniques focus on injecting malicious work items into task queues, timer queues, and I/O completion queues.
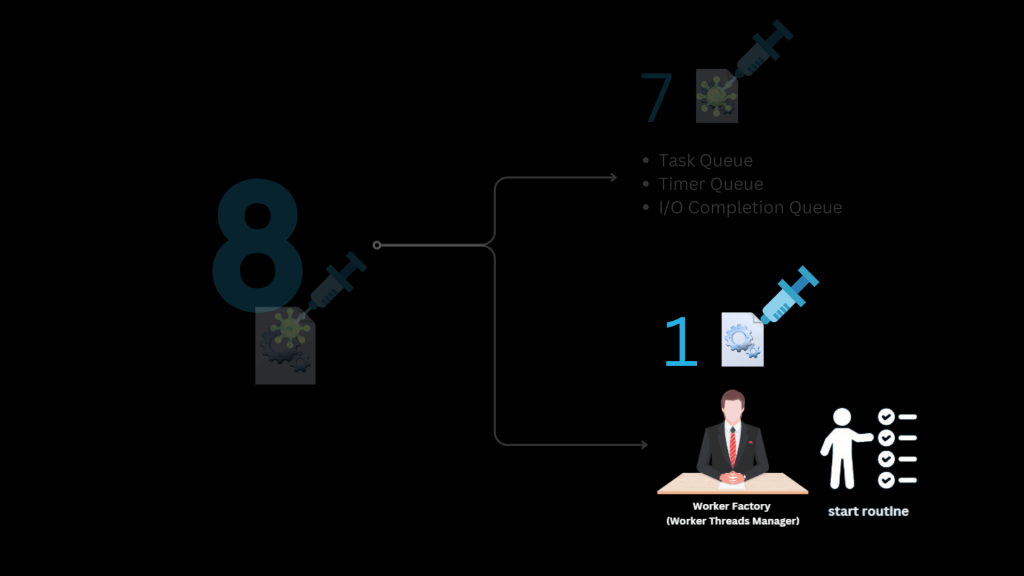
In this blog, we’ll only focus on the first technique – the start routine manipulation – and save the remaining seven for future posts.
The Injection Technique
Here’s the high-level approach the researchers used:
- Study system calls to interact with the Worker Factory Object.
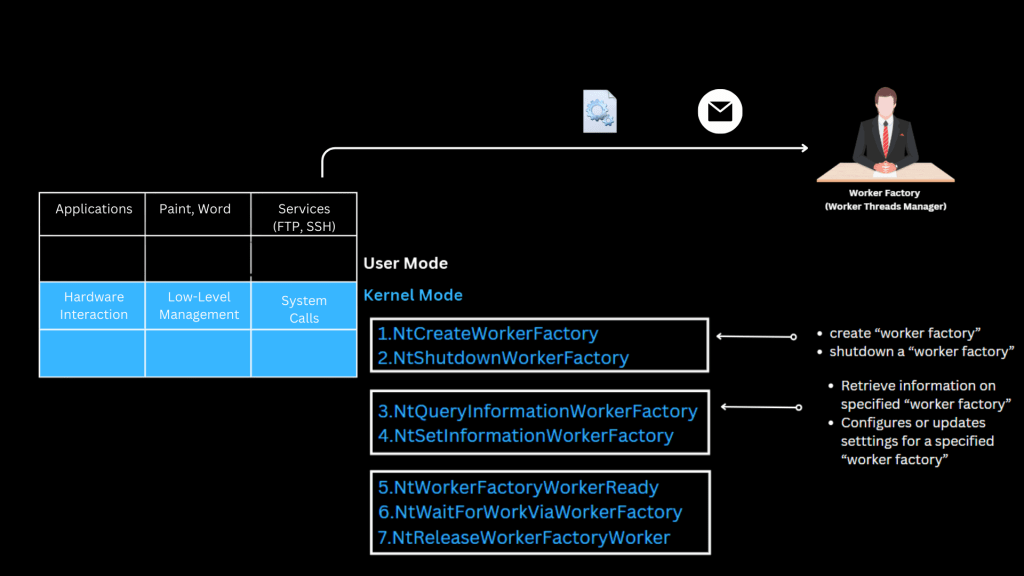
2. Get a handle to the Worker Factory Object using DuplicateHandle — a legitimate API with many benign use cases.
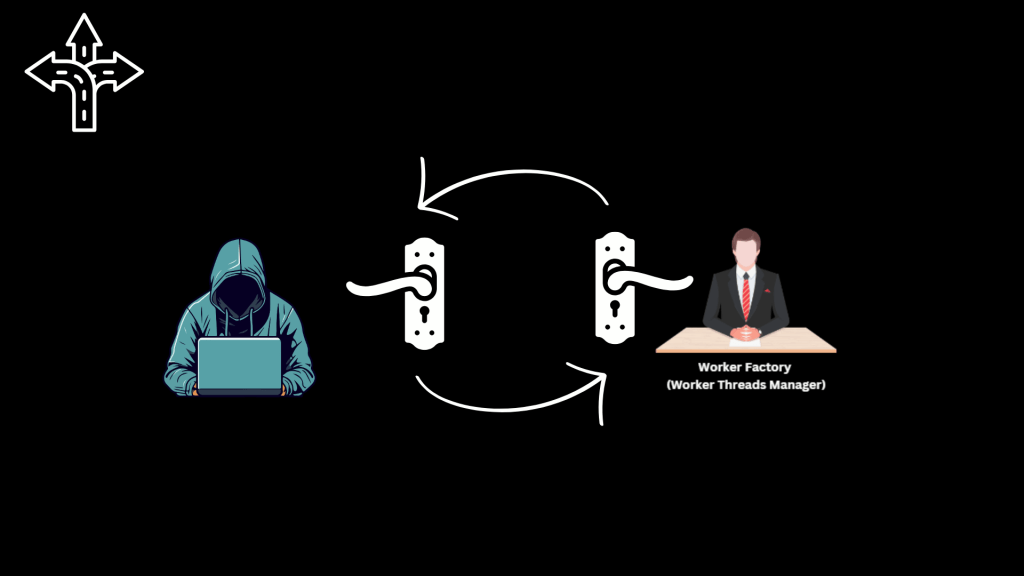
3. Query the Worker Factory using undocumented syscalls like NtQueryInformationWorkerFactory to retrieve the Start Routine Value (memory address of the routine).
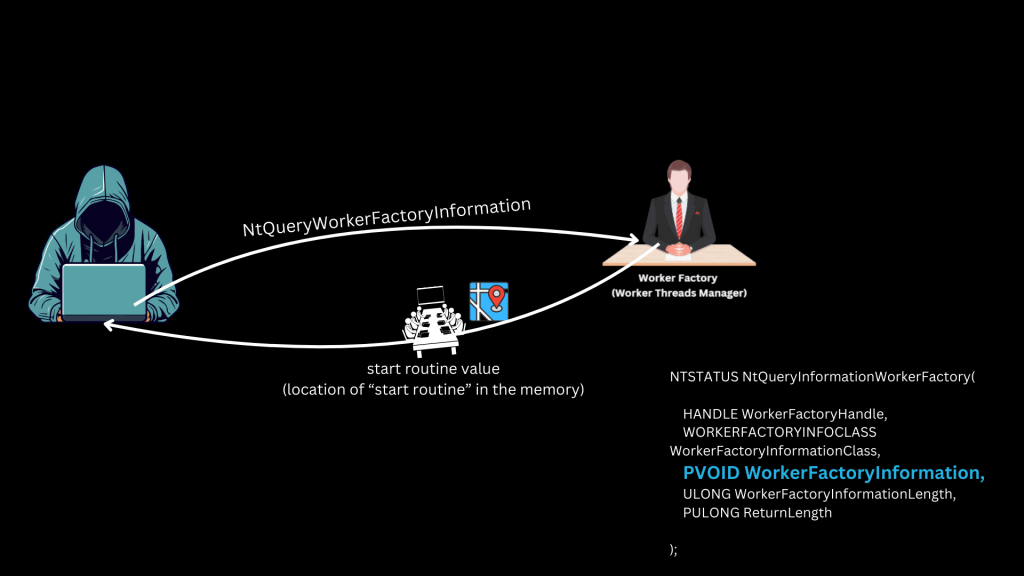
4. Overwrite that memory location with attacker-controlled shellcode.
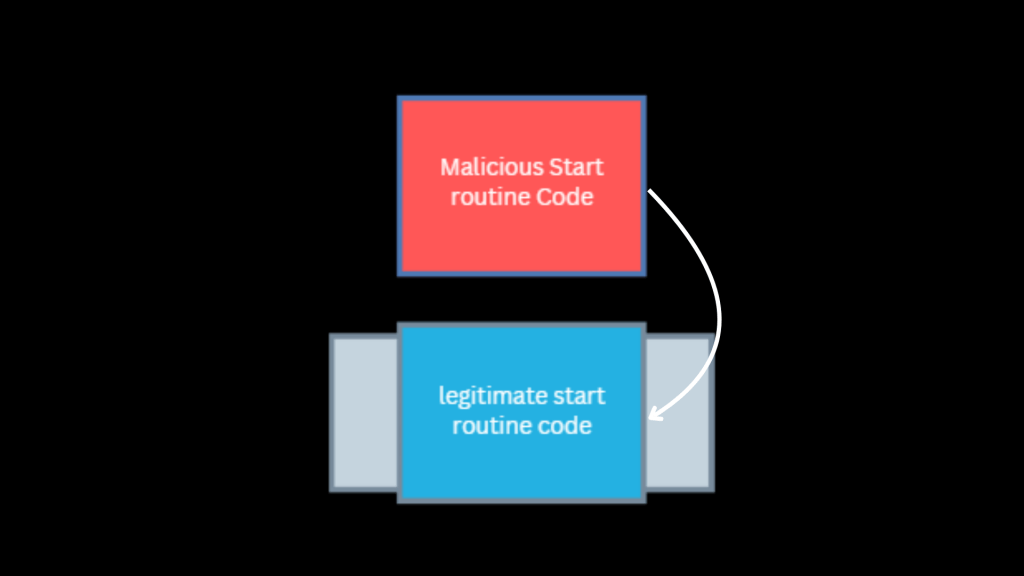
Let the thread pool execute the new malicious routine naturally — without calling any suspicious APIs.
No direct execution. No alarms. Full stealth.
Why This Works
Because the execution happens naturally within the target process, no API like CreateRemoteThread is called. The malicious payload is simply waiting in the right place, and when the time comes, the thread pool executes it — thinking it’s a legitimate task.
This completely bypasses behavior-based detection, which expects some form of suspicious API use at execution time.
Closing Thoughts
This wraps up the Advanced Malware Tactics – Process Injection blog series.
If you’ve followed along from Part 1 to Part 5, you now have:
- A solid foundation in Windows memory architecture and APIs
- A clear understanding of process injection techniques
- Real-world examples of malware like Qakbot using DLL injection
- Exposure to undetectable next-gen injection using thread pool abuse
This knowledge is essential for malware analysts, SOC defenders, reverse engineers, and cybersecurity professionals who want to stay ahead of modern threats.
If you found this series helpful, check out the full video course on Udemy for additional visuals, quizzes, and narration. Stay sharp, and I’ll see you in the next deep dive!
References & Credits
This blog post is based on the groundbreaking research presented at Black Hat Europe 2023. Full credit goes to the original researchers for their responsible disclosure and detailed technical analysis.
Primary Sources:
- Research Presentation: “Pool Party: Exploiting Windows Thread Pools for Process Injection”. Presented at: Black Hat Europe 2023
- Research Blog (SafeBreach): “The Pool Party You Will Never Forget: New Process Injection Techniques Using Windows Thread Pools.” Author: Alon Leviev
- GitHub Repository (Proof of Concept): PoolParty PoC code for research and educational purposes. GitHub: https://github.com/SafeBreach-Labs/PoolParty
Disclaimer:
This post is created for educational and awareness purposes only. The techniques discussed here are based on responsible public disclosures and should only be studied in controlled lab environments.



Leave a comment