Welcome to Part 2 of our blog series on Advanced Malware Tactics – Process Injection. If you haven’t read Part 1, we recommend starting there first, as it lays the groundwork with key Windows internals.
In this post, we’ll introduce the concept of process injection — one of the most widely used detection evasion techniques by attackers. This is a short overview to prepare you for the more technical deep dive coming up in Part 3.
Why Attackers Rely on Evasion
Gaining initial access to an organization’s network is often the easy part. Social engineering, phishing, or exploiting a known vulnerability can do the trick. The real challenge for attackers begins after they’re inside — during the post-exploitation phase.

This is where EDR systems, antivirus tools, and security monitoring software come into play. The attacker must now hide their presence, avoid detection, escalate privileges, and execute malicious payloads — all without raising alarms.

That’s where process injection enters the scene.
What is Process Injection?
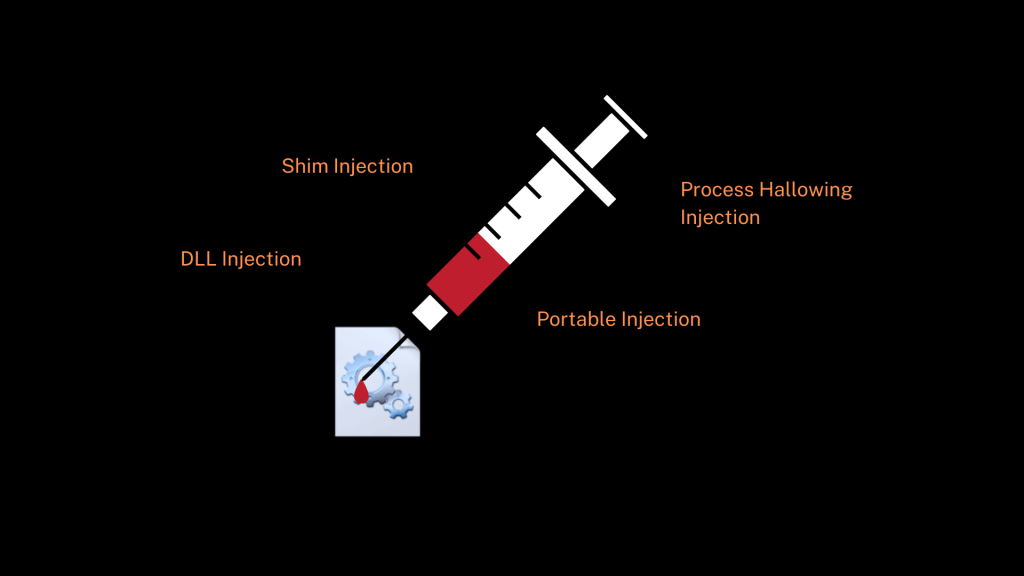
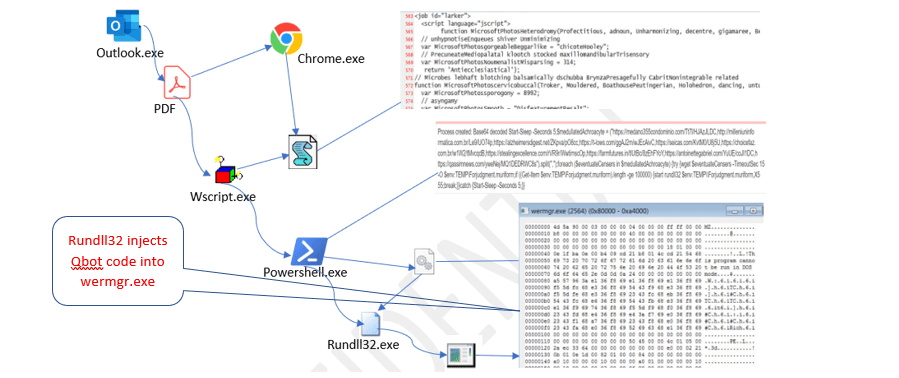
Process injection is a technique that allows an attacker to execute arbitrary code inside the memory space of another process. This lets the malicious code run under the disguise of a legitimate application, making it much harder to detect.
Imagine hijacking a delivery truck to transport your own packages. To the outside world, it still looks like a trusted delivery service — but what’s inside has changed.
How Does It Work?
Every process in Windows is assigned a virtual address space. Attackers attempt to:
- Allocate space inside a legitimate process
- Write their own malicious code into that space
- Execute the code using Windows APIs or system calls
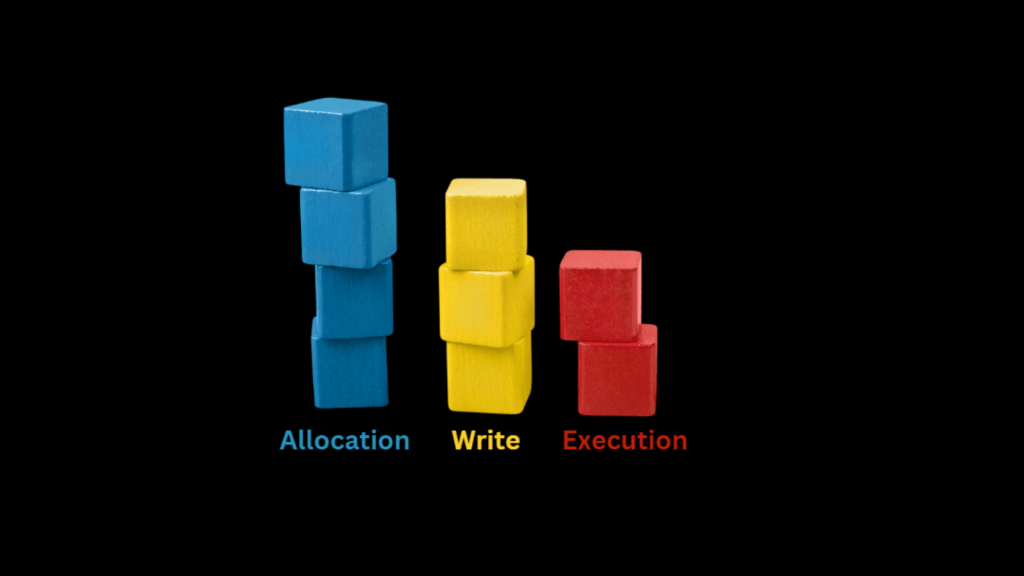
These three steps — Allocation, Writing, and Execution — are the building blocks of process injection. Every variant, no matter how advanced, relies on this same foundation. Think of them like structural pillars holding up every injection technique.
We’ll explore each of these in depth in Part 3.
This short overview gives you a high-level understanding of what process injection is and why it matters. In the next post, we’ll dig deeper into the technical building blocks behind it — so stay with us.


Leave a comment